Glean on AWS: Connecting to on-premises services over Shared TGW
The Glean AWS project can peer with TGWs in your other AWS accounts. This allows Glean to crawl private services within your network. Within the Glean project, we use a transit VPC network to minimize IP collisions with your network and minimize exposure. You must set aside a private /26 range for this transit VPC.Topology
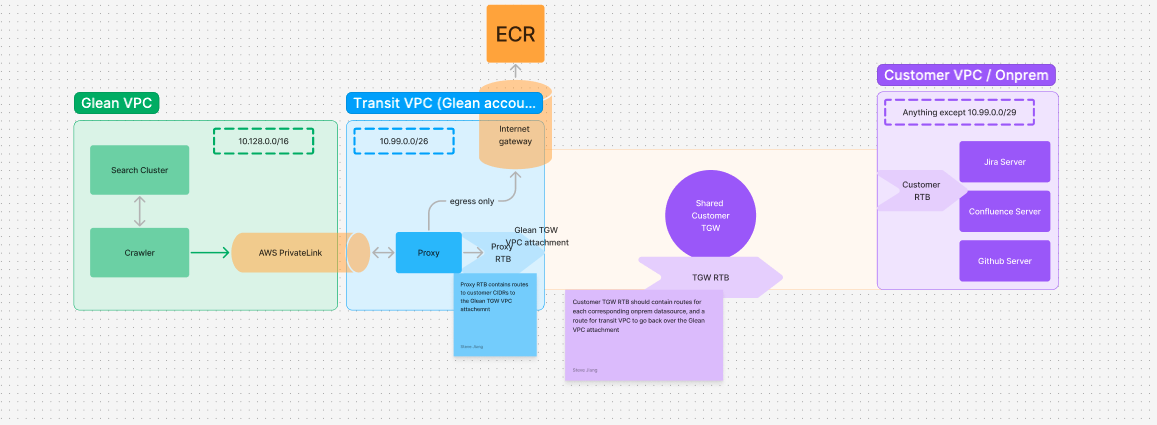
Configuration steps
You do not need to touch anything within the Glean account. All configuration will be done through terraform; you need to ensure routes and security groups are properly set up on your datasource or networking accounts.
- To start configuring Glean shared TGW connectivity, first decide on a transit network
- The set-aside /26 IP CIDR range for Glean’s use that doesn’t conflict with Glean VPC (10.1.0.0/16) or any existing customer ranges and provide this to Glean
-
This is used to avoid IP collisions
- Create a resource share with the corresponding Glean account, sharing the TGW resource with the principal:
arn:aws:iam::{glean-account-id}:root - You can either accept the resource share on the glean account manually and provide the accepted transit gateway id
- OR if you would like the Glean account to make the connection request, provide the resource share to glean and glean will create an outgoing connection request, which you will need to accept and let glean know once done
- Glean will create a TGW attachment to the shared TGW. You will need to accept this attachment and set up routes from there.