What Code Writer Is
Code Writer is an AI-powered coding agent that:- Runs inside your own dedicated Glean project and VPC.
- Automatically identifies and attaches to the right repositories for each task, using your GitHub integration and configuration.
- Clones repos, makes changes, runs checks, and opens PRs as you, under your Git identity.
- Fully respects your existing branch protections, CODEOWNERS, and approval flows.
- Runs the Claude Code CLI in a loop, writing code and checking its work.
- Factors in any instructions you have set in your repo’s
CLAUDE.mdor.codeagentfiles.
Core Security Guarantees
Code Writer is designed around strict guarantees:- Data residency: All execution happens in your dedicated Glean project and VPC. Source code and IP stay in your cloud.
- Network control: Pods cannot talk directly to the internet. All outbound traffic goes through a locked-down HTTPS egress proxy with a very small domain allowlist (GitHub + required cloud APIs).
- Isolation: Each run gets its own gVisor-sandboxed Kubernetes pod, non-root user, and dedicated resources.
- Least privilege & attribution: All Git operations use the triggering user’s identity and permissions, preserving your existing controls and audit trails.
- Zero-day runtime retention: Pods, workspaces, and in-pod state are destroyed at the end of the session. The runtime keeps no long-lived state by default.
Data Residency & Privacy
All Code Writer jobs run in customer-dedicated clusters tied to your Glean project and VPC. Strong isolation prevents one customer’s runtime from reaching another customer’s resources, and one Code Writer session from accessing another session’s workspace. Repositories are cloned directly into the pod from your GitHub App integration and are not copied into external multi-tenant indexing services. Orchestration and model calls are initiated from within your VPC. Requests follow your configured routing (for example, your chosen cloud AI endpoint) and your networking controls (private service connect, firewalls, VPC-SC, etc., if enabled).Identity, Authentication & Git Operations
On first use, each user links their GitHub account through Glean. Their personal GitHub token is encrypted at rest in Glean’s credential store and redacted from logs and error messages. We fetch the latest valid credential and expose it only via a secure injection path in the proxy/ICAP layer. Tokens are not written into the pod filesystem. PRs and commits are authored as the real user, so branch protections, CODEOWNERS, and required reviewers still apply. There is no elevated “super bot” identity that can bypass your policies.git blame and audit logs correctly identify who triggered each change, which supports incident response and compliance.
Optional GPG commit signing is available via a dedicated bot identity. The private key is stored encrypted (SecretStore to Kubernetes Secret), mounted into pods as a locked-down file (for example,
/etc/gpg/private.key), and commit metadata is derived from the key (and can be overridden by policy). Without a signing key, Code Writer uses a standard identity but still preserves per-user PR authorship.Network Security & Egress Controls
All outbound traffic from Code Writer pods is forced through a namespace-local HTTPS proxy. Pods themselves have no direct internet access.- Network policy: Pods can egress only to DNS and the proxy (for example, port 3128).
- Session credentials: Each Code Writer session has its own proxy credential; unauthenticated traffic is dropped.
- Credential injection: GitHub tokens are not stored in the pod. Git traffic goes through a secure proxy/ICAP path, which injects credentials just-in-time and restricts them to the specific repo and to non-admin operations.
- Repository isolation: Attempts to push to other repos or perform admin operations (webhooks, collaborators, settings) are blocked.
- Domain allowlist: Only a small set of domains is allowed (for example,
github.com,aiplatform.googleapis.com,accounts.google.com,oauth2.googleapis.com). Only HTTPS (443) is allowed; HTTP (80) and IP literals (for example,https://192.0.2.1/) are blocked. RFC1918 ranges are blocked to prevent access to internal/private services. - Fail-closed: Any non-allowlisted domain, IP, or pattern is denied by default.
Ingress Controls
Code Writer pods are not exposed via public Kubernetes Services or Ingress. Only two internal callers are allowed:- The orchestrator that manages job lifecycle.
- Glean’s Query service, over authenticated internal channels.
Runtime Isolation & Container Security
Each Code Writer session runs in a dedicated, hardened pod:- gVisor sandboxing adds a kernel-level isolation layer between the container and the host.
- A non-root user (for example, uid 1000) is used for Git and process execution.
- Resource limits ensure predictable CPU and memory usage.
- An ephemeral workspace with zero-day retention is used: the repo is cloned into a session-scoped directory, and when the session ends, the pod and its storage are destroyed. In-pod runtime state is not retained beyond minimal operational logs.
- Secret management: Sensitive values (GPG keys, ephemeral tokens, etc.) are delivered via Kubernetes Secrets and are never baked into images.
Credentials & Secrets Handling
User GitHub tokens are encrypted at rest in Glean’s credential store, never embedded in URLs or checked into code, and used via secure proxy injection scoped to a single session. GPG keys are stored encrypted and synchronized as Kubernetes Secrets, then mounted read-only with least privilege. The working tree never contains credentials, and hooks and configuration avoid writing secrets into.git/config or source files. This reduces the risk of accidental credential leakage via Git history, logs, or artifacts.
Architecture Diagram
The following diagram illustrates the secure flow from developer request to GitHub PR: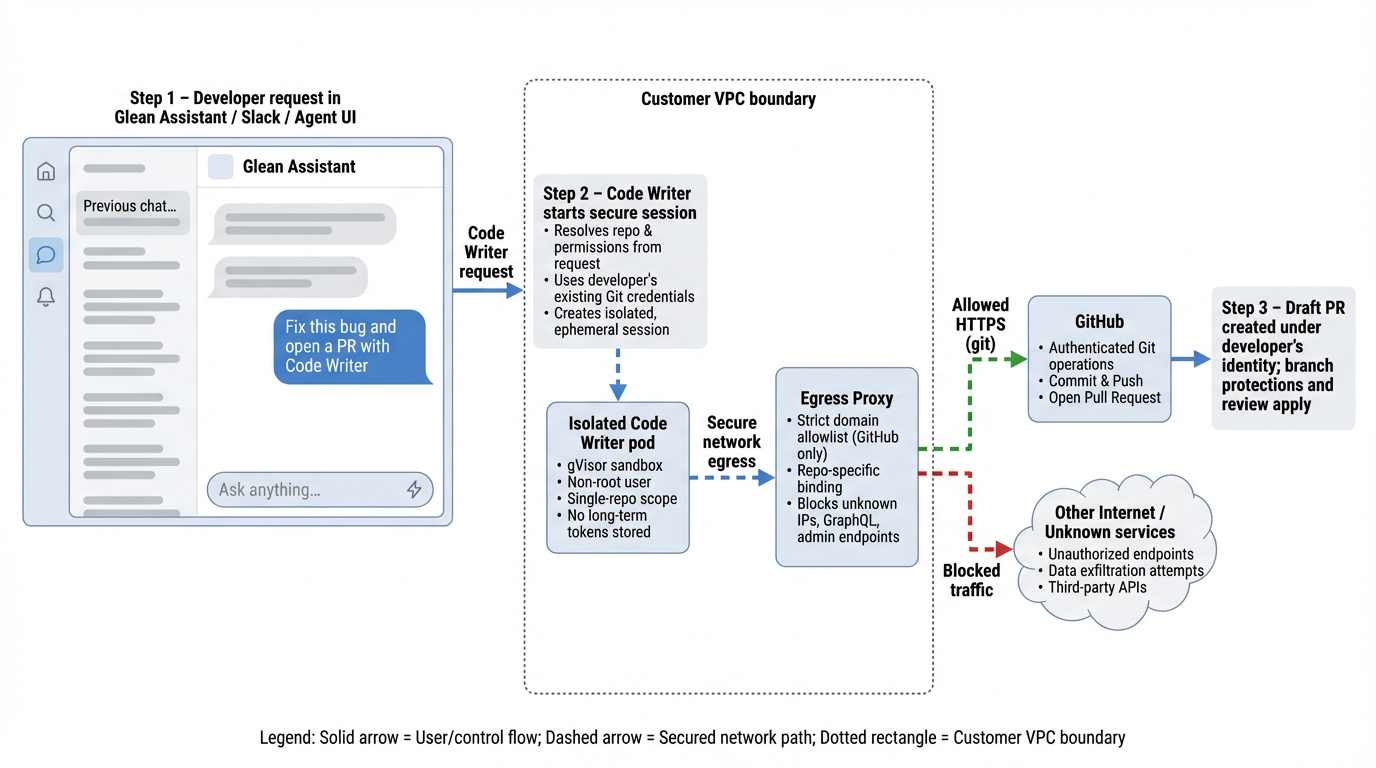
Architecture flow explanation
Architecture flow explanation
- Developer request: The developer initiates a request in Glean Assistant, Slack, or the Agent UI.
- Secure session creation: Code Writer resolves repo and permissions from the request, uses the developer’s existing Git credentials, and creates an isolated, ephemeral session.
- Isolated Code Writer pod: The pod runs in a gVisor sandbox with a non-root user. No long-term tokens are stored.
- Secure network egress: All traffic goes through the egress proxy with a strict domain allowlist (GitHub only). The proxy enforces repo-specific binding, single-repo scope, and blocks unknown IPs, GraphQL admin endpoints, and unauthorized operations.
- GitHub operations: Authenticated Git operations (commit, push, open pull request) are performed under the developer’s identity.
- Blocked traffic: Other internet destinations, unknown services, unauthorized endpoints, data exfiltration attempts, and third-party APIs are blocked.
- Draft PR created: The pull request is created under the developer’s identity; branch protections and review requirements apply.
Threat Model & Mitigations
Prompt injection and data exfiltration
- Risk: Malicious content convinces the agent to send code, logs, or secrets to an attacker.
- Controls: Strict egress proxy and domain allowlist, RFC1918 blocking, no IP-literal access, and NetworkPolicies that only allow DNS and proxy traffic.
Supply chain attacks
- Risk: Compromised dependencies or tools via registries.
- Controls: Pre-built base image with required tools (git, gnupg, bash, Node.js), regular vulnerability scanning and patching, and an egress proxy that blocks access to non-allowlisted registries and hosts.
Credential leakage
- Risk: Reading environment variables or configs with secrets and leaking them over the network or into logs.
- Controls: Egress restrictions, secure credential injection that avoids long-term storage in pods, and logs designed to avoid printing raw secrets.
Internal network access
- Risk: Using Code Writer as a pivot to reach internal APIs or metadata endpoints.
- Controls: RFC1918 and IP-literal blocking at the proxy, NetworkPolicies restricting egress to DNS and proxy only, and no access to node metadata endpoints from pods.
Custom Images (BYO Image)
Custom images are an optional, advanced feature that can be enabled for your instance. If you are interested in this capability, please talk to your Glean account team or support contact to discuss your use case and have it turned on.
Audit Logging & Automatic Cleanup
Code Writer is designed to integrate with your existing audit and logging practices while minimizing residual risk through automatic cleanup.Audit logging
- Code Writer uses your existing Git hosting provider, so PRs, commits, and comments appear in your normal audit trails.
- All Git actions run under the triggering user’s account, so every change is traceable.
- Kubernetes, proxy, and backend logs capture session start and end, network access decisions, and authentication and credential injection events.
- Logs are designed to avoid raw credentials or large volumes of source code; sensitive values are redacted where possible.
Automatic cleanup
- Each session uses its own pod, which is automatically destroyed when the run completes.
- Cloned repos and temporary files are removed along with the pod, enforcing zero-day retention of in-pod state by default.
- Session credentials used for network egress or Git access are scoped to a single run and are not written to disk inside the container.
By combining dedicated projects and VPCs, tight network egress controls, strong pod isolation with zero-day runtime retention, and per-user identity, Code Writer is designed to deliver the benefits of AI-assisted development without weakening your security, compliance, or data residency posture.