Connect to GitLab Server
The instructions below will work for on-prem instances that the Glean Crawler can access. Glean supports deployments on both GCP and AWS. Your on-prem GitLab Server instance must be network-accessible to the Glean crawler running in your cloud. Please reach out to Glean Support for any network configuration required.Code Search is enabled by default after GitLab Server is connected to Glean. The previous code action toggle in the Admin console has been removed. See Code Search for more details.
Step 1. Determine API access token scopes
To authorize our API calls, we need a personal access token from a GitLab admin account. This account must have access to all projects that you’d like Glean to crawl. For this API token, if you’re willing to grant us the api scope, we can programmatically create webhooks during setup. If you want to restrict the token to read-only access, you will need to manually create webhooks for every single project that you want crawled. Supported Objects: GitLab Server connector supports merge requests, issues, wikis, commit messages, and code (for use in Glean Assistant).Step 2. Create a personal access token
- Sign in to your GitLab admin account.
- Navigate to the upper right hand corner (user icon) and click “Preferences”
- Select “Access Tokens” on the left side menu.
-
Add a personal access token.
- Name: Glean Token
- Scopes:
- if you’re allowing write privileges
- api
- if you’re only allowing read privileges:
- read_user
- read_api
- read_repository
- if you’re allowing write privileges
- Leave Expires at empty
- Copy the personal access token into the corresponding field in Glean
- Check the box if the token has write privileges
Step 3. Provide information about your GitLab server instance
- Your GitLab instance domain name (e.g. https://gitlab.company.com)
- Your GitLab Server IP
Step 4. Create Webhooks Manually (if token has only read access)
If your personal access token does not have theapi scope, you must configure webhooks so GitLab Server can send change events to Glean.
Log in to GitLab with an admin account that can configure webhooks.
Prerequisites:
- For group webhooks, you must have the Owner role for the group.
- For project webhooks, you must have at least the Maintainer role for the project.
Group webhooks (recommended) apply to all projects within a group and its subgroups, while project webhooks apply only to individual projects.
- Navigate to the group or project page within GitLab.
- From the left-side menu, go to Settings → Webhooks**.
- Select Add new webhook.
- Configure the webhook:
- URL: Use the URL shown in the GitLab data source setup page in Glean (Show setup instructions).
- Secret token: Use the token as shown in the setup instructions.
- Triggers:
- Comments
- Issue events
- Merge request events
- Wiki page events
- Save the webhook.
- In Glean, enter the same secret token in the Webhook secret token field for the GitLab Server data source.
System Hook
Lastly, create a system hook so Glean receives certain repository-level events:- In GitLab, navigate to Admin Area → System Hooks.
- Create a system hook with:
- URL: Use the URL shown in the GitLab data source setup page in Glean (Show setup instructions).
- Secret token: Use the same token you used for the webhooks.
- Triggers:
- Repository update events
- Merge request events
- Save the system hook.
Step 5. Upload User Mapping to GCS
GitLab doesn’t return a user’s email via the API unless that user has explicitly allowed their email to be publicly shown. In order for us to correctly crawl permissions in GitLab, we need to be able to map each user id to their company email.-
Please create a CSV with two columns: GitLab user ID, and email. The CSV doesn’t need to have column headers, but the columns do need to be in the order (user ID, email).
- Note that the user ID is NOT the username –– the user ID should be numbers only and corresponds to the
idin the example response of the /members API. - Example of a correct row:
12345,user1@glean.com
- Note that the user ID is NOT the username –– the user ID should be numbers only and corresponds to the
- Provide this CSV to your Glean support team to correctly map the user IDs to the primary SSO email.
Appendix
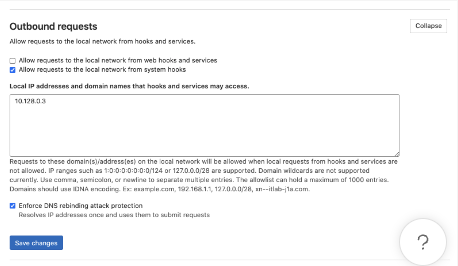
If you want to direct webhooks through local network, before creating webhooks, we’ll need to allow local requests to the local network from web hooks and services:- Navigate to Admin Area → Settings → Network
- Expand Outbound requests
- Paste the local proxy IP into the text box under “Local IP addresses and domain names that hooks and services may access.” (Glean Support can help you with finding this IP)
- Click Save changes